Ask&Do™ - The transactional relationship that gives life to email
Over email, we can ask someone to do something, and we can be asked to do something, too.
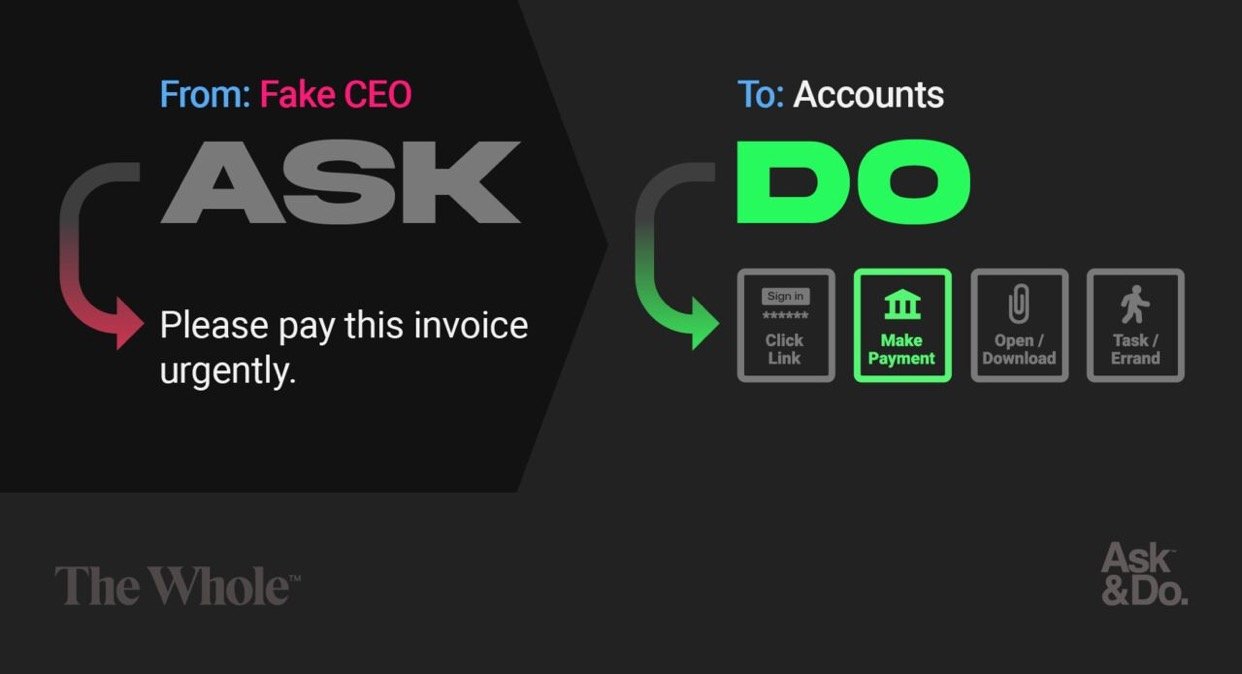
We can be asked to do anything, theoretically. But I think it helps to define the actions, and the best balance of simplicity and not wanting to leave things out is below. These, are the Do Do Do Dos! Or four Dos, if you’re in a rush.
Now the four Dos also happen to be the four things scammers want you to carry out. If you’re doing any of these, there’s some risk involved.
To make you do them, they need to adopt the identity of someone - or a brand/service - that you trust to ask you.
So straightaway you can start to quantify identities that can tap into these ‘actions’. Let’s take ‘make a payment’; at work who can ask you to process a payment? And the answer to that is also who a scammer will want to pretend to be.
On the flip side, what can you ask others to do? In your Organisation can you ask someone to go and turn off the electric fence? If so, a scammer might even pretend to be you. If they need access to that ‘Do’ (Task/Errand) then as you they can ‘ask’ it.
Services are selfish
It’s interesting to note that the dynamic becomes almost entirely one-sided when the email is from a service. Say your Bank. They can ask us to ‘do’ things, like login, but we can’t ask them anything, at least not over email.
This is why phishing emails are so suited to scammers. It taps into the trust, and the ability to ask us to do things, that already exists. And it requires no interaction, or getting into character - they know what to put as it’s exactly what we all see in our inboxes every day.
Does Asking and Doing ever not feature?
I tried to break the theory, but I think it’s fairly universal. Even sending a blank email is in a round about way asking someone to notice it’s arrived. And an automated receipt is sort of asking you to keep it for your records, so it’s hard to find a time it doesn’t work, even if it needs a little more of a lateral interpretation.
Does it have a wider security use?
Perhaps, but maybe more as a way of having a consistent and simple way to see the communication channels and authority dynamics.
You could take a specific ‘click link / login’. And then choose an individual, or a role, and establish who or what can ask them to do it. It might not highlight anything new, but at the very least from a security education perspective it makes it easier to explain the threat vectors someone might be exposed to. It might even highlight that a valuable process has too many who can do the asking, and the process needs adjusting.
Really it’s just an easy way to take a person, role or action, and quickly find the dynamics and transactional relationships surrounding it.
Ask&Do™ - The dynamic at work
Here’s a video that uses just me, and my very patient girlfriend! It shows the concept and relationships at work.
This features in my security awareness training series here
© 2024 James Linton